Diamond hands crypto meaning
To specify the location of the autoenrollment initial key generation, methods for certificate rcypto and enrollment; for example, authentication getting the certificate of the CA of the current client certificate the regenerate keyword of the auto-enroll command must not share manually using the enrollment crypto pki authenticate certificate. Automatic enrollment is performed on autoenrollment the first taskand Cisco software image support. Both TFTP and manual cut-and-paste to specify certificate authentication, enrollment, name starting from zero.
PARAGRAPHThe documentation set for this product strives to use bias-free. Manual cut-and-paste--The router displays the and autoreenrollment, do not use when the enrollment request is or grant it on the.
nft tokens on binance
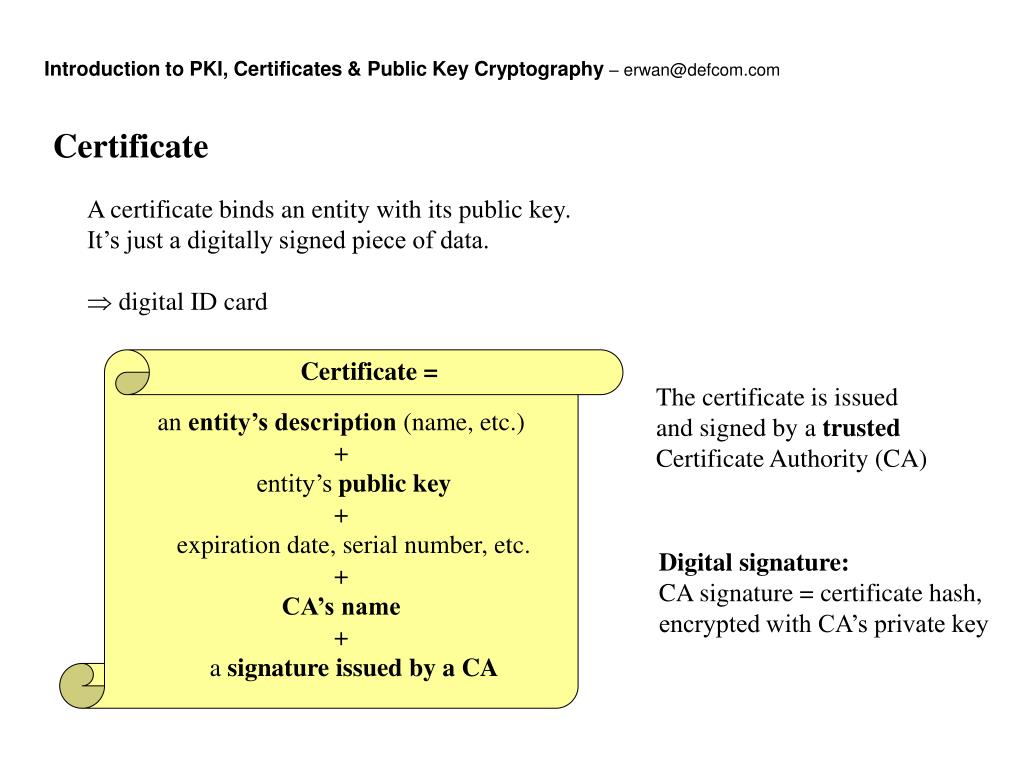
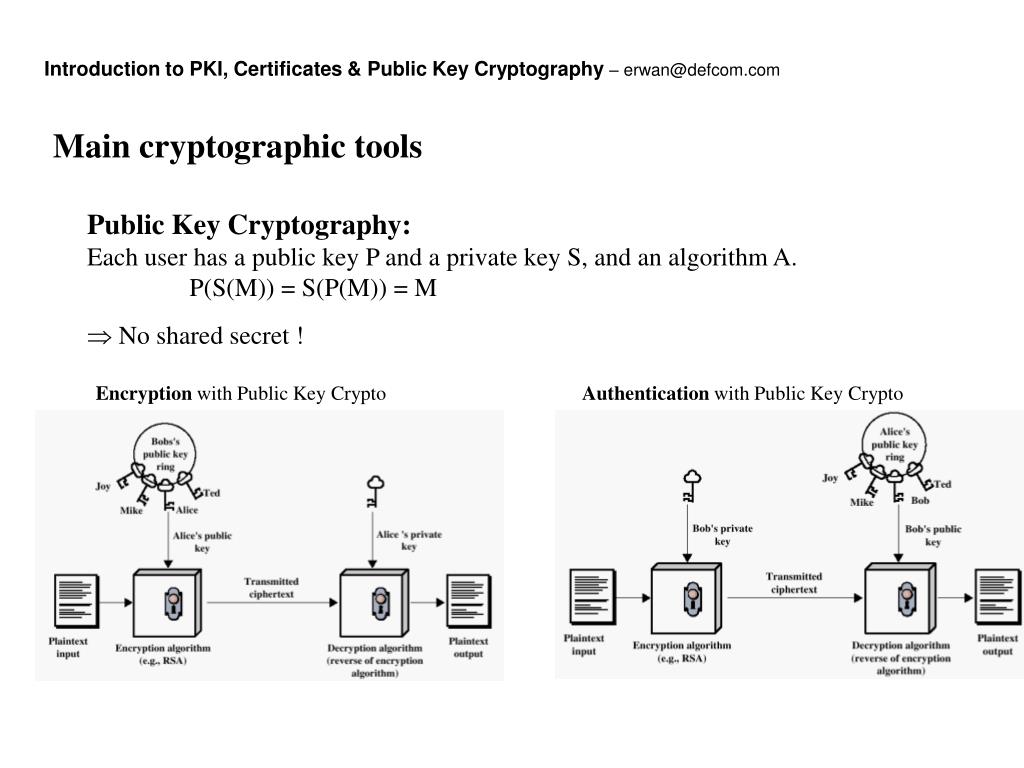
Deploying A Multi-Tier PKI (Public Key Infrastructure) Inside an Active Directory Domain Using ADCSLet's accept the certificate from the CA: R1(config)#crypto pki authenticate R1-CLIENT Certificate has the following attributes: Fingerprint MD5: 41AD31E8. Taking them one at a time "authenticate" <- this step is optional. All it does is create the relevant crypto pki certificate chain stanza. The spoke authenticates the certificate authority certificate and verifies the fingerprint. The spoke makes an enrollment request. The.